The Zero-Trust Era: How Companies Are Rewriting Security Rules
For decades, cybersecurity relied on a simple idea: if you’re inside the corporate network, you’re trusted. But in a world of remote work, cloud ecosystems, and relentless cyberattacks, that assumption has become dangerously outdated. Today’s organizations are embracing a new philosophy—Zero Trust—that flips traditional security on its head.
Zero Trust doesn’t mean “trust no one”; it means trust nothing by default. Every user, device, and connection must continually verify itself, no matter where it is or where it’s going. This shift marks a profound transformation in how companies design, manage, and enforce security.
Here’s how the Zero-Trust era is rewriting the rules for modern enterprises.
1. From Perimeter Defense to Continuous Verification
Traditional security models relied heavily on perimeter defense—firewalls, VPNs, and network segmentation. Once inside, users had broad access.
Zero Trust replaces that with a simple but powerful principle:
Never trust, always verify.
Validation becomes:
- continuous (not one-time at login)
- contextual (based on user role, device status, and behavior)
- adaptive (access changes dynamically as risk changes)
This eliminates the “castle-and-moat” mindset and treats every request as a potential threat.
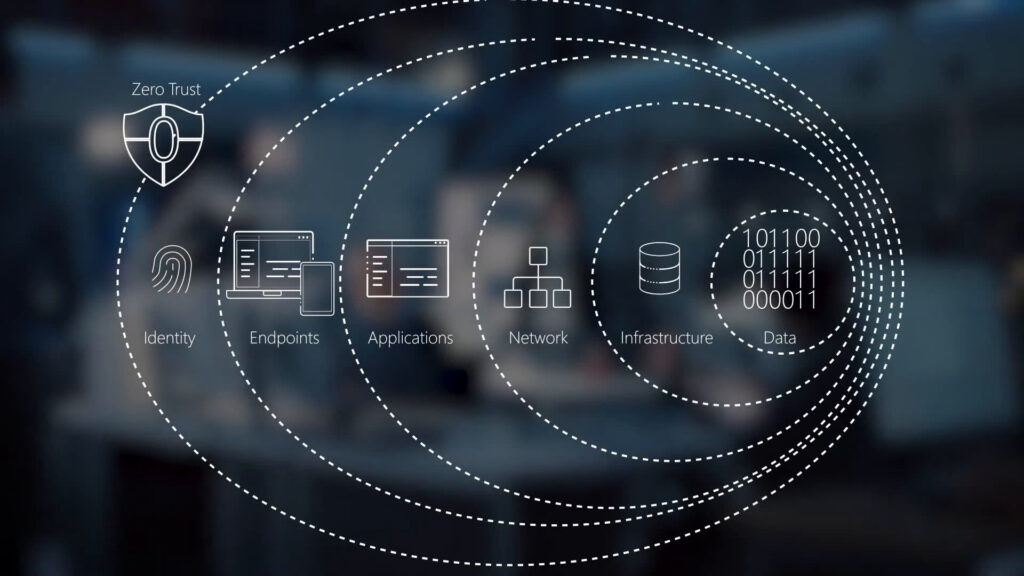
2. Identity Becomes the New Perimeter
In a Zero-Trust world, identity is the core control plane.
Companies are investing in:
- multi-factor authentication (MFA)
- passwordless logins
- identity threat detection
- role-based and attribute-based access
- unified identity platforms for employees, customers, and partners
Access is granted only when identity, device, and context all align—preventing compromised accounts from escalating their privileges unnoticed.
3. Devices Must Prove They Are Clean and Compliant
Zero Trust requires every device to be authenticated and evaluated before accessing resources.
Enterprises monitor:
- operating system health
- security patches
- endpoint protection status
- unusual behavior or IP reputation
- device ownership and configuration
If a laptop is out of date or acting suspiciously, access can be reduced or revoked instantly.
This approach turns endpoint management into a frontline defense, not an afterthought.
4. Microsegmentation Limits the Blast Radius
Instead of giving broad access to entire networks, Zero Trust deploys microsegmentation—dividing resources into isolated zones.
Benefits include:
- attackers can’t move laterally
- infections stay contained
- sensitive data is tightly siloed
- access control becomes granular
Even if a hacker breaches one system, Zero Trust makes it extremely difficult to move beyond it.
5. Stronger Security for a Remote and Hybrid Workforce
With employees now working from home, cafes, airports, and co-working spaces, traditional network perimeters have dissolved. Zero Trust is the only model flexible enough to secure modern workflows.
Key changes include:
- secure access regardless of location
- reduced reliance on fragile VPN tunnels
- encrypted connections for every action
- automated threat detection and user monitoring
Zero Trust ensures people can work from anywhere—without putting the organization at risk.
6. Cloud and SaaS Adoption Make Zero Trust Essential
Cloud infrastructure has multiplied the number of entry points and increased complexity.
Zero Trust helps companies:
- secure multicloud environments
- manage SaaS sprawl
- enforce consistent policies across providers
- prevent misconfigurations (a major breach cause)
Instead of trusting cloud environments implicitly, Zero Trust requires them to meet the same verification standards as on-prem systems.
7. AI and Analytics Power Real-Time Decisions
Zero Trust isn’t possible without intelligence.
Modern platforms use AI to:
- detect anomalous behavior
- score user and device risk
- flag suspicious login attempts
- identify compromised credentials
- predict emerging threats
The system learns from patterns, allowing security rules to adapt in real time.
8. Zero Trust Requires Cultural Transformation—not Just Tools
One of the biggest misconceptions is that Zero Trust is a product companies can buy.
In reality, it’s a strategy and mindset shift that touches:
- IT
- security
- leadership
- compliance
- employees
Training, collaboration, and consistent policy enforcement are essential for success.